Making Symantec (Norton) AntiVirus update when logged out
Norton AntiVirus (now Symantec AntiVirus) is not, out of the box, able to automatically update it’s virus definitions or it’s application when running on a Macintosh. Symantec has posted two articles that, when put together, let you have all of your Macs update in the dead of night while they are logged out. I’ve been using this technique on all of the Macs in my computer labs for over a year with great success.
The two articles are Running LiveUpdate using UNIX commands and Scheduling LiveUpdate for all users using UNIX commands.
Putting the information from these two articles together you can set up your Macs to auto-update using this procedure.
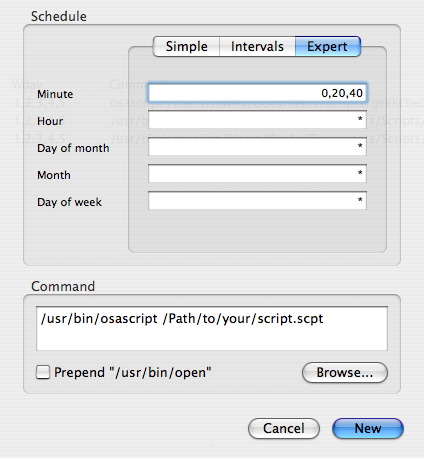
We’re going to set up a root-level cron job to run a command to update the things we need. I like to have it run around 3 AM. If you don’t know how to do it at the command line use Cronnix and edit the System cron job.
First we’ll cover the basic flag options you have.
-liveupdatequiet
If you don’t want that annoying LiveUpdate window to pop up (especially since you’re logged out) you need the -liveupdatequiet YES flag. If you do want it to show then leave this flag out.
The default action is to show it. However, if you are running this when the machine is logged out you could come in the next morning to a lot of machines with the LiveUpdate window showing behind the login window.
-liveupdateautoquit
If you want LiveUpdate to automatically quit when it’s done use the -liveupdateautoquit YES flag.
I’m not sure why you WOULDN’T want it to quit when it’s done.
Update options
To tell LiveUpdate what to update you have to choose from these options with the -update flag.
LUal = All Symantec products
LUdf = Norton AntiVirus virus definition updates
LUlu = LiveUpdate
LUna = Norton AntiVirus
Putting it all together
So, putting this all together, an example command to silently update the virus definitions would look like this. Watch out for line wraps. This should all be on one line:
/Applications/Symantec\ Solutions/LiveUpdate.app/Contents/MacOS/LiveUpdate -update LUdf
-liveupdatequiet YES -liveupdateautoquit YES
Things to watch out for
One “gotcha” to look out for. Symantec changed the name of the folder that holds LiveUpdate between versions 9 and 10. So, the above example will work in version 10. To have it work in version 9 use this path:
/Applications/Norton\ Solutions/LiveUpdate.app/Contents/MacOS/LiveUpdate
A second thing to watch out for is when you use the LUal option. If the actual AntiVirus or LiveUpdate applications get updated you’ll need to restart the machine. Norton will give your users an error message when they log in if the machine hasn’t been rebooted since the update.
For that reason I only update the virus definitions this way. When the actual applications need updating I run the command using the LUal flag using Apple Remote Desktop’s “Run UNIX command” function on all the machines at once and then restart them.
admin :: Mar.29.2007 :: Management, System, Terminal :: Comments Off on Making Symantec (Norton) AntiVirus update when logged out